OKV 21.9 Concept notes:
url: https://docs.oracle.com/en/database/oracle/key-vault/21.9/okvag/okv_concepts.html#GUID-9A18985D-B7B7-499A-8920-1E00CDB52A50
Endpoints: computer systems where security objects are needed to access the data. The security objects must be efficently managed
Endpoints needs to be enrolled to communicate with OKV
Related security objects can be added to a virtual wallet for ease of wallet management.
Endpoints always have a default wallet, so they become the default virtual wallet if no explicit wallet creation is done.
Deployment architecture:
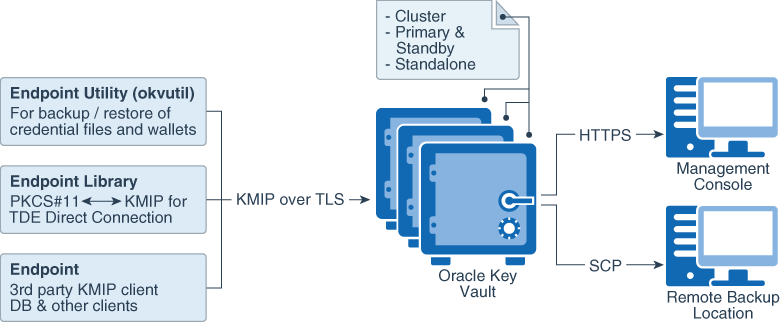
1. Appliance (OKV<RDBMS & GG<Oracle Linux)
2. Standlone or multimaster with upto 16 nodes (2 of which needs to be RW pair)
3. Large enterprise : Multimaster with multiple nodes needs to be considered.
4. For small single DC (data doesnt leave the DC): single read-write pair (2x OKV) needs to be considered
5. Standalone deployments can be used for testing and development purposes
Access control & grants:
Users < access at security object leve or virtual wallet level
grouping of users and endpoint is also possible - this way user group and end point groups get access.
access controls: read, write, delete
# 3 categories of access controls:
1. Read only
2. Read & Modify - grants read and modify access to the security object
3. Manage Wallet - user should already have read and modify permission + with this role, user grant the permission to other users/endpoint (groups) and also delete the security object/wallet or change its description
Seperation of duties:
Key vault admin: manage security objects and maintain the lifecycle of the security object
System admin : OKV backup/recovery/enroll endpoint/create users and groups, stop/start keyvault,setting up and managing a cluster
audit admin: audit related tasks, has read access on all security objects, manage audit settings
endpoint administration roles: create, manage endpoint (groups) -- these are non administrative roles.
Less privileged endpoint permissions:
endpoint specific : create/manage - system admin owned
endpoint group specific: create/manage - key vault admin owned
These less privileged can be granted to users who didnt create the security object as well.
Admin Roles | super privileged roles |
System Admin | OKV stop/start, OKV backup/restore, Create/Manage endpoint/user, Setup/Manage Cluster |
Key vault admin | Create/Manage endpoint groups, Maintain security objects lifecycle |
Audit admin | audit related tasks, has read access on all security objects, manage audit settings |
Non Admin role privileges |
|
|
|
|
|
|
|
|
|
|
|
|
Privilege or role | type? | Who owns this role? | Description |
Create endpoint | system | owned by system admin role | create & manage endpoint (auto granted, can be revoked)
system admin role, even if revoked from a user, they can still
manage the endpoints they created. Just that they cant create new endpoints.
System admins only can revoke create endpoint permission from others.
user with create endpoint permission on deletion has no impact on the endpoints they created. The management responsibility of the endpoint goes to system admin role if no one else with manage that endpoint exist in the system |
Manage endpoint | object | owned by system admin role | Allows users to reenroll, suspend, delete, resume endpoints
System admin only grant/revoke this role. If system admin role is revoked from a user, the manage end point permission goes away, unless create endpoint granted at that time of the endpoint creation from the admin; default wallet can be set by the user. Deletion of the user with manage end point; will lead to either system admin or other user with same manage endpoint to manage the endpoint. |
Create endpoint group | system | owned by keyvault admin | user with create endpoint group auto gains manage end point group as well as soon admin creates a endpoint group; but that can be disabled seperately. As like endpoint create system permission, the system admin role revokation wont remove manage endpoint group permission for those end point groups created by them; grant/revoke only OKV admin can do this; deletion of user will lead to other end point managers to manage the group or okv admin manages the request. |
Manage endpoint group | object | owned by keyvault admin | manage all the endpoint group operations, adding the endpoint group from/to other groups; delete endpoint group. The endpoint group inherits permission as users from wallet. Only OKV admin can grant/revoke the permission; inheritance flows from user group to user or endpoint group to the group/user'. deletion of endpoint group will lead to other end point managers to manage the group or okv admin manages the request. |
Object naming convention:
users - [a-z,A-Z],[0-9],[_]
groups, user groups, wallets, endpoint - [a-z,A-Z],[0-9],[_][.][-]
users, usergroups, endpoint, endpoint group - case insenstive
Virtual wallet is case sensitive
Recover passphrase: setup during install, it is needed during mutlimaster node addition , when all admin users not available, backup/restore; only way to recover this credential is to reinstall OKV.
recovery passphrase | Once lost, the OKV needs to be reinstalled. This passphrase supports
1. new node addition
2. backup/restore |
root user | ssh disabled, also only needed during patching & maintenance only |
support user | ssh is enabled, it is the common tty linux terminal user |
End point managers | permission to provision end point |
End point admin | It by default has create & manage endpoint. In case needed we can regrant the *group permision as well. So this user becomes single user to manage all endpoint related operations |

No comments:
Post a Comment